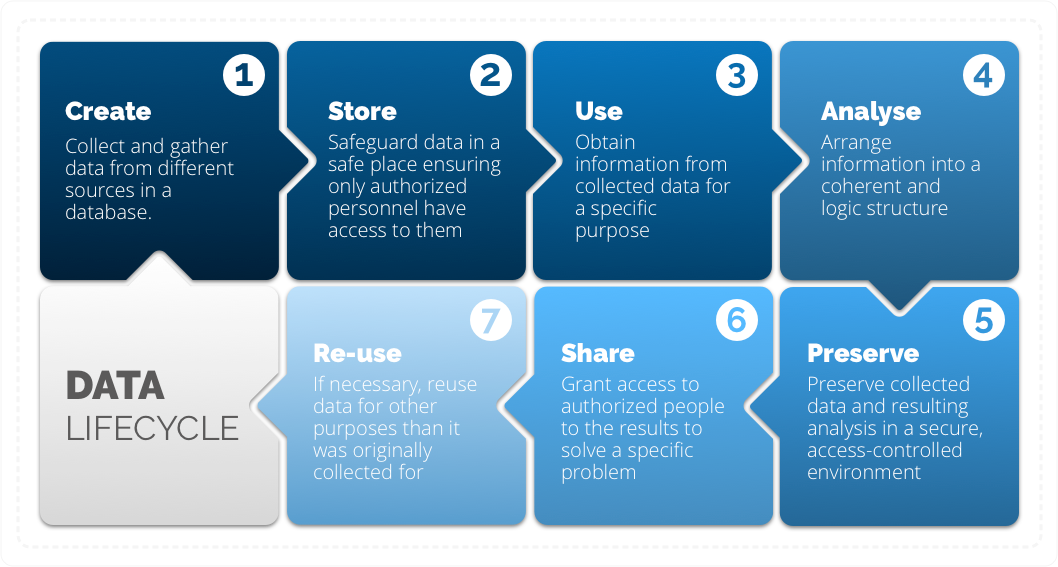
Data Lifecycle

CRIM helps you unlock the potential of all types of data
Speech - Audio
Text
Video - Image
Structured data
Geospatial
Time series
At the heart of business success
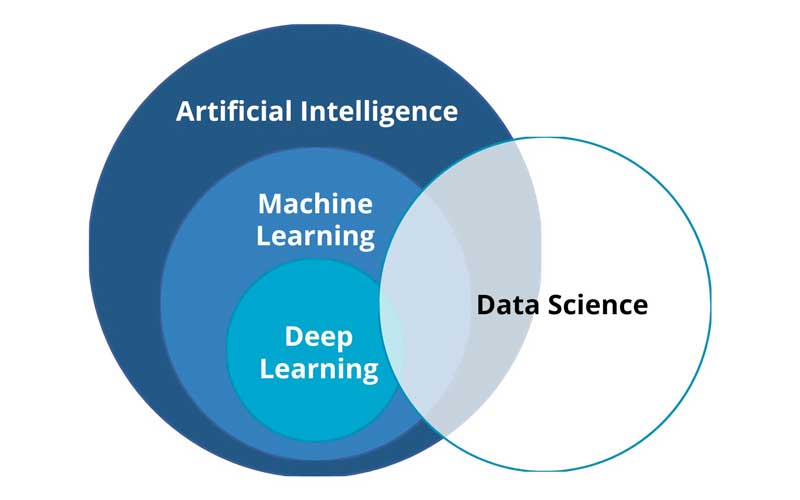
Data science is an interdisciplinary field that covers several areas of artificial intelligence. It is at the heart of any technological innovation and value-added project to ensure organizations’ sustainability.
CRIM experts apply their know-how to answer your questions and carry out projects based on data processing.
Data integrity and compliance
Organizational transformation and innovation initiatives can only happen with quality data. Data is no longer the mere result of business processes but an asset. Business people are taking more responsibility for their data, using it more intensively in contexts that are not necessarily the ones initially intended. Data is collected from various sources and is cross-referenced to generate value. This makes data governance essential to preserving data integrity and compliance.
CRIM’s expertise in the area of compliance and data integrity is structured around the following:
- Regulatory compliance with provincial laws (including Quebec’s Act Respecting the Protection of Personal Information in the Private Sector), federal laws (including Canada’s Personal Information Protection and Electronic Documents Act), and international standards (such as the European Union’s General Data Protection Regulation);
- The overall accuracy, completeness, and consistency of data;
- Data security, i.e. protection against external attacks: The motivation for this new cross-cutting expertise comes from the evolution of data status: it is now at the heart of many decisions and organizational transformations (analytics, business intelligence, artificial intelligence, automation, etc.).
This expertise takes the form of tangible outcomes and applications, such as:
- Voice biometrics
- Deepfake detection
- Analysis of user behaviour and applications
- IoT cybersecurity and the detection of malware















